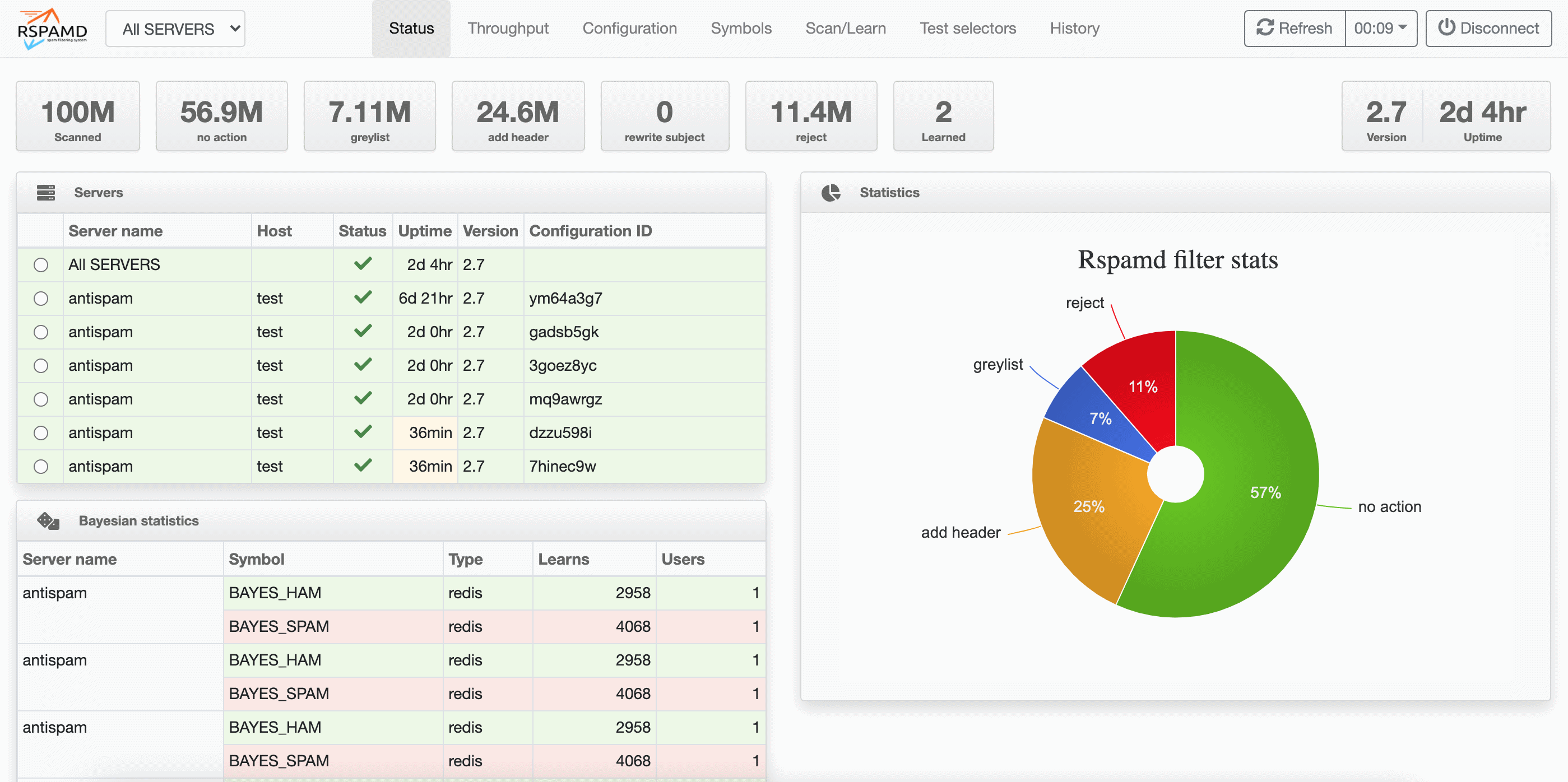
Rspamd is the best open source anti-spam solution we’ve used, both in terms of speed and accuracy. The fuzzy storage feature in Rspamd blows SpamAssassin out of the water—even if you’re boosting SpamAssassin with other solutions. Unfortunately, cPanel doesn’t support Rspamd, so if you stick with cPanel, you’re left with a second-rate filter or forced to rely on third-party inbound filtering or a separate gateway. Luckily, Enhance Control Panel supports Rspamd natively. It’s a powerful, lightweight spam filter that handles large volumes of mail with ease and impressive precision—but only if trained and configured correctly. Rspamd is only as good as your setup and the data you feed it.
Rspamd stays quietly in the background, running as a permanent process and using the milter protocol to scan every email your server sees. It runs dozens of checks and spits out a score—higher scores mean more likely spam. If it smells like spam, scores like spam, it’s probably spam.
Now, the default version shipped with Enhance is great, but if you’re the kind of admin who likes being ahead of the curve, this guide is for you. We’re going to upgrade Rspamd to the latest version and enable the WebUI (https://rspamd.com/webui/) so you can tweak its settings, train it like a spam-detecting Jedi, and enjoy that clean inbox goodness.
So grab a coffee, open up your terminal, and let’s dive in.
Step 1: Check Your Current Version
root@my:~# rspamadm --version
Rspamadm 3.8.1
Outdated, huh? Let’s upgrade from version 3.8.1 (Jan 26, 2024) to the latest 3.11.1 (March 8, 2025).
Step 2: Upgrade Rspamd
apt update
sudo apt-get install -y lsb-release wget gpg
CODENAME=`lsb_release -c -s`
sudo mkdir -p /etc/apt/keyrings
wget -O- https://rspamd.com/apt-stable/gpg.key | gpg --dearmor | sudo tee /etc/apt/keyrings/rspamd.gpg > /dev/null
echo "deb [signed-by=/etc/apt/keyrings/rspamd.gpg] http://rspamd.com/apt-stable/ $CODENAME main" | sudo tee /etc/apt/sources.list.d/rspamd.list
echo "deb-src [signed-by=/etc/apt/keyrings/rspamd.gpg] http://rspamd.com/apt-stable/ $CODENAME main" | sudo tee -a /etc/apt/sources.list.d/rspamd.list
sudo apt-get update
sudo apt-get --no-install-recommends install rspamd
If you’re prompted about config file changes, say yes—but be sure to back up your custom configs first if you have any.
Step 3: Verify the Upgrade
root@my:~# rspamadm --version
Rspamadm 3.11.1
Perfect. You’re now running the latest version of Rspamd. This upgrade resolves several issues commonly seen with spam filtering on Enhance and introduces a bunch of powerful new features. You can explore the full changelog here:
https://github.com/rspamd/rspamd/releases/tag/3.11.1
Rspamd also comes with excellent documentation. If you plan to fine-tune your setup manually, we highly recommend going through it:
https://rspamd.com/doc/configuration/
Using cPFence? Good news, you don’t have to worry about the heavy lifting. Our New Spam AutoShield module handles the complex configurations and training for you—just keep following along.
Step 4: Securely Accessing the Rspamd WebUI via SSH Tunnel
Rather than exposing the Rspamd WebUI to the internet, a safer approach is to access it through an SSH tunnel from your local machine. This method keeps the interface accessible only to you—perfect for quick tweaks without compromising server security.
1. Generate an SSH Key (If You Don’t Already Have One)
On your local machine (Linux, macOS, or Windows PowerShell), run:
ssh-keygen
Just press Enter through the prompts to accept the defaults.
2. Copy Your Public Key to the Server
If you’re using Linux or macOS:
ssh-copy-id root@your-server-ip
On Windows, ssh-copy-id isn’t available, use:
type $env:USERPROFILE\.ssh\id_rsa.pub | ssh root@your-server-ip "mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys"
3. Create an SSH Tunnel and Access the WebUI
Run this from your local machine:
ssh -L 11334:127.0.0.1:11334 root@your-server-ip
Then, open your browser and go to:
http://localhost:11334
Just keep that terminal session open while you’re using the interface.
Tip: If you want direct access without using an SSH tunnel:
Edit the Rspamd config file:
nano /etc/rspamd/rspamd.conf
Replace localhost:11334 with 0.0.0.0:11334 in the controller section:
worker "controller" {
bind_socket = "0.0.0.0:11334";
Then restart Rspamd:
systemctl restart rspamd
Now open the port for the Rspamd GUI:
sudo ufw allow 11334/tcp
sudo ufw reload
Access the Rspamd web UI directly at:
http://your-server-ip:11334
Now you can log into the new shiny Rspamd WebUI.
Update on 24-jun-2025:
Rspamd 3.12.1 introduced changes that may affect WebUI access, particularly how the controller worker binds to IPs and how configuration overrides work.
If changing the bind_socket in rspamd.conf has no effect, edit the following file:
nano /etc/rspamd/override.d/worker-controller.inc
Replace:
bind_socket = "127.0.0.1:11334";
with:
bind_socket = "0.0.0.0:11334";
Then restart Rspamd:
systemctl restart rspamd
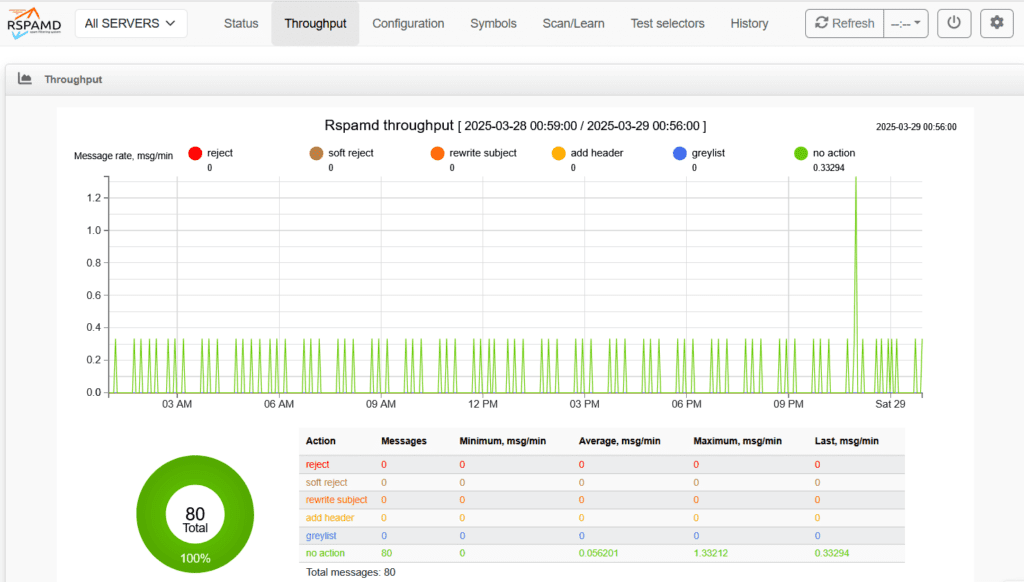
Step 5: Change the Default Controller Password
It’s strongly recommended to change the default controller password—whether or not you plan to use the WebUI. This is highlighted clearly in the official Rspamd documentation, and it’s a simple but important step to secure your setup.
Generate a password:
pwgen 16 1
Let’s say it gives you:
eiLi1lueTh9mia4
Now hash it:
rspamadm pw
Paste in the password and you’ll get something like:
$2$g95ywihfinjqx4r69u6mgfs9cqbfq1ay$1h4bm5uod9njfu3hdbwd3w5xf5d9u8gb7i9xnimm5u8ddq3c5byy
Now create the config file:
nano /etc/rspamd/override.d/worker-controller.inc
Add:
password = "$2$g95ywihfinjqx4r69u6mgfs9cqbfq1ay$1h4bm5uod9njfu3hdbwd3w5xf5d9u8gb7i9xnimm5u8ddq3c5byy";
Restart Rspamd:
systemctl restart rspamd
Step 6: Using the Rspamd WebUI: Scan & Train Like a Pro
Now that your WebUI is live, let’s make the most of it. Head over to the Scan/Learn tab—this is where the real training happens.
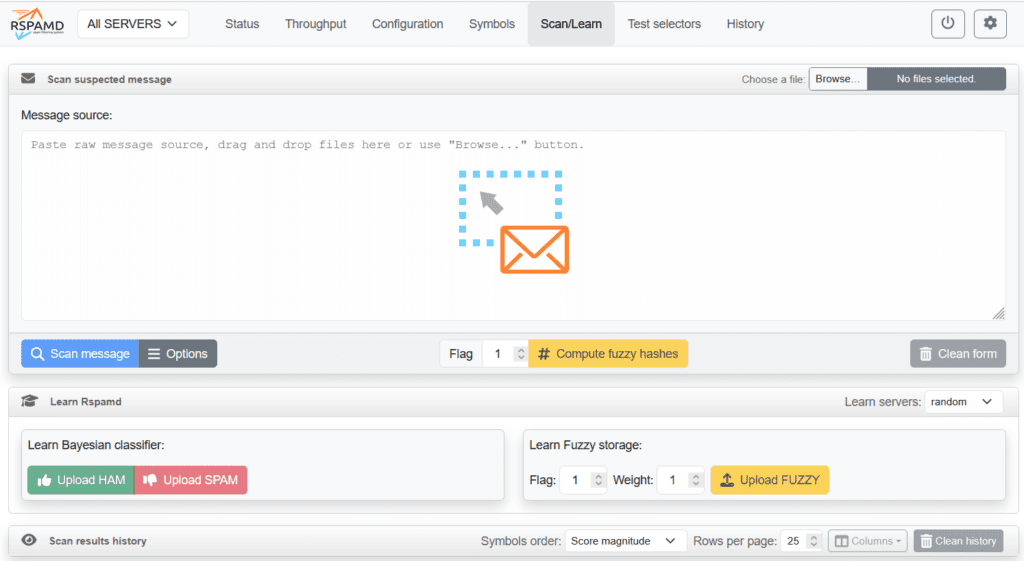
- Scan a Message
Got a suspicious email? Just paste the raw message source or drop in an.emlfile. Click Scan message and Rspamd will run it through its filters, showing you exactly how it was scored and why. - Train the Bayesian Classifier
This is where Rspamd learns what’s good and what’s garbage.- Hit Upload SPAM to feed it confirmed spam.
- Use Upload HAM for legit emails.
The more you train, the smarter it gets—like a spam-fighting AI pet.
- Fuzzy Hash Learning
Fuzzy hashing helps detect spam variants that try to sneak past with small changes.- Use Upload FUZZY to train it on known spam samples.
- You can adjust the Flag and Weight, but defaults work fine for most.
Fuzzy storage is what makes Rspamd so much more effective than traditional filters.
Combining Bayesian learning with fuzzy hashing gives Rspamd a serious edge—it doesn’t just block known spam, it adapts and evolves with it.
Reviewing Message History
The History tab is your window into Rspamd’s decision-making. Every scanned email gets logged here with detailed scoring and action info.
- You’ll see the sender, recipient, subject, spam score, and final action taken (e.g.,
no action,reject, oradd header). - Click any entry to expand and see which symbols (rules) were triggered—like
FORGED_SENDERorMIME_GOOD—and how much each contributed to the total score. - You can sort results by score magnitude, value, or name to find the most suspicious or highest scoring emails.
This view is super helpful for tuning your rules, identifying false positives, and understanding why a message was (or wasn’t) flagged.
And that’s it. Your Enhance server now has the latest Rspamd with the WebUI up and running. Go forth and train it to fight spam like a pro.
Want Smarter Spam Protection Without the Manual Work?
If you’re ready to take your Rspamd setup beyond the basics, our new cPFence Spam AutoShield module delivers a full-stack solution in three powerful steps.
First, it automatically configures and optimizes your mail server for better spam filtering—no more digging through confusing config files or trying to tune milters by hand. Mail server tuning is usually a pain, but not with cPFence.
Second, it tackles Rspamd’s biggest strength—and weakness: training. Rspamd is only as good as the data you feed it, and manually uploading spam and ham takes time. Spam AutoShield solves this by instantly training your filter with over 170,000 spam samples, so you get smarter detection with zero effort.
Third, it equips you with powerful tools to block spam at the source. Whether it’s a sender IP, domain, specific email, subject match, or even sketchy TLDs—you’re in control of what gets through, across your entire server.
Check out the full feature list and creative use cases here:
Spam AutoShield®: Total Server-Wide Spam Control for Enhance Servers







No comment